Teaching Information Evaluation Skills
Genie Tyburski
Originally published in The CyberSkeptic's Guide to Internet Research (February 2005) under the title, "To Catch a Hoax." Updated 14 August 2006.
Through educational Web sites, workshops and just-in-time one-on-one training opportunities, librarians instruct people on how to evaluate information before they act on it. We repeatedly caution about assessing the credibility of a source and the importance of verification. Yet surveys and anecdotal evidence suggest that suspect Web sites fool people time and again.
The parody site Gatt.org, for example, once duped the Center for International Legal Studies into believing it was the Web site of the World Trade Organization. Accordingly, a few years ago, the association arranged for someone from the parody site to speak at its annual conference. The speaker -- an imposter from an activist group known as the Yes Men -- offended several attendees with racist remarks. A staged pie-throwing incident followed the presentation, and the fiasco later culminated in the faked death of the speaker/imposter.
More recently, information published at the hoax site Dihydrogen Monoxide Research Division (DHMO) nearly caused a California city to issue an ordinance banning water. When news broke about the Council's gullibility, one official blamed a paralegal for conducting "bad research."
Online Fraud Goes High-Tech
As if instructing on the characteristics of credible information were not a sufficient challenge, criminals up the ante by employing Internet technology to perpetrate online fraud. A recent Federal Trade Commission (FTC) survey, "Consumer Fraud in the United States," (August 2004) found that "nearly 25 million adults in the U.S. -- 11.2 percent of the adult population -- were victims of one or more of the consumer frauds covered by the survey during the previous year." Fourteen percent of fraud victims first learned about the scam through e-mail or a Web site.
But today's phishing scams -- one type of online fraud -- could drastically increase this percentage. Phishing is a technique that lures people, usually via e-mail, into providing their personal or financial information. It can result in identity theft or unauthorized charges against credit or banking accounts.
The Anti-Phishing Working Group (APWG), an association devoted to eliminating these scams, counted 116 unique attacks in December 2003. By October 2004, the number of unique attacks for the month totaled 1142 -- a whooping 884% increase.
The sharp increase stems in part from the success of these scams. Reporting on a survey it conducted during April 2004, Gartner Inc. found that 3% of those questioned had been lured into revealing financial or other personal information as a result of a phishing attack. The APWG "Phishing Activity Trends Report" for October 2004 estimated that "up to 5%" of consumers respond to the scams. The Gartner survey also showed that phishing attacks cost consumers $2.4 billion. Another study conducted by the anti-spam firm Mailfrontier concluded that e-mail spoofing fools recipients about 28% of the time.
The need for assessment skills is obvious. But as criminals employ more sophisticated deceptive techniques, people need preventive strategies as well as information on how to detect technical tricks. Teaching the usual criteria for identifying quality in information -- scope of coverage, accuracy, objectivity, authority and timeliness -- is no longer sufficient. Moreover, some of the advice (for example, evaluate the appearance of a Web site) no longer offers adequate protection.
Helpful Evaluative Skills
Phishing scams and hoax Web sites often fool people because they look like the real McCoy. Regarding the DHMO Web site, I received this question by e-mail:
How can you tell this site is a Hoax when it looks so official? This is probably a stupid question.
In fact, the question is not a stupid one. The Web site's official look lends credence to the information. It also makes it dangerous.
People need three basic evaluative skills. First, they should know how to identify the source of the information and assess its expertise. Second, they should be able to recognize common technical tricks used to make information appear as something it isn't. Third, they should know how to verify the information.
The Information Quality teaching Web on The Virtual Chase addresses the first and third skills. See, in particular, the checklist entitled "How to Evaluate Information."
The second skill -- recognizing common technical tricks -- is one that librarians often fail to address. We frequently explain the importance of finding dates on Web pages, for instance, but neglect to warn about coding that automatically displays the current date.
One method for detecting this particular trick involves opening the source code of the Web page. In Internet Explorer, select View/Source from the menu. Then search it (Control+F) for the date exactly as it appears. If the date reads, October 12, 2004, you should enter October 12. The browser's Find function will report no match, if a script generates the date. If you search the month without the day, and the script appears in the Web page coding, you might find the actual date-generating script.
Tricks Used in Phishing Scams
Familiarizing the public with tricks used in phishing scams would go a long way toward preventing online fraud. It might also make consumers savvier buyers of legitimate goods and services.
A few months ago, I visited the online store of a major computer vendor and discovered it was transmitting the buyer's payment type (not the credit card number) and shipping information without encrypting the data. While the vendor recently fixed this security bug, the practice is not uncommon.
You can detect this flaw by looking for the lock icon, which should appear in the lower right-hand corner of the browser window. If no lock appears -- even if the Web site address begins with https:// -- the data you submit is not encrypted.
If a lock displays, double-click it to open the certificate. Make sure the supplier of the site's security matches what you expect to find. If you are transmitting financial information, check the encryption level (Details tab). One hundred twenty-eight bit (or 1024 bits) encryption currently provides the best level of security.
Of greater concern than the submission of unencrypted personal information -- in part because it's harder to detect -- is the number of Web sites vulnerable to cross-site scripting attacks. Cross-site scripting occurs when an external source injects code into the target source.
In a phishing scam, the malicious external source might use this technique to replace all, or a portion, of the target site. The technique might plant a bogus form that redirects financial data transmissions to a server controlled by the criminals. A recent survey by the United Kingdom-based computer consultancy group Next Generation Security found that 90 percent of the financial Web services audited contained design flaws, which made them susceptible to cross-site scripting attacks.
Phishing Attacks in Action
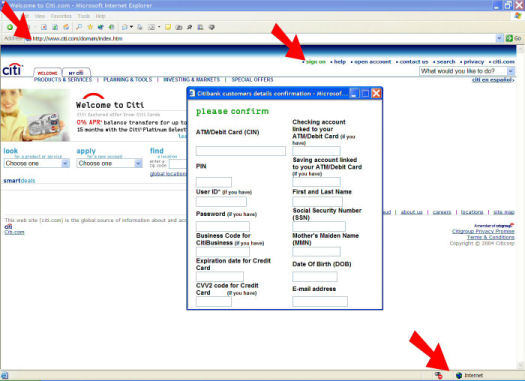
The phishing scams illustrated in the two screen shots targeted Citi and US Bank. The attack on Citi customers used script to load the real Citi Web site behind the bogus pop-up. The pop-up then redirected data to the criminals' Web server. In the US Bank scam, the criminals copied the bank's Web site and spoofed its Web address.
Several indicators in both cases exposed the fraud. Both requested financial or confidential information, but neither displayed a lock icon.
The actual Citi Web site, behind the malicious pop-up, prompted the customer to sign in. But it's illogical to request personal or financial information when you don't yet know whether the visitor is a customer. Moreover, the bogus pop-up accepted false data. You could make it go away by entering any information in each of the fields. Conversely, it would not close unless you completed the form or disconnected from the Internet.
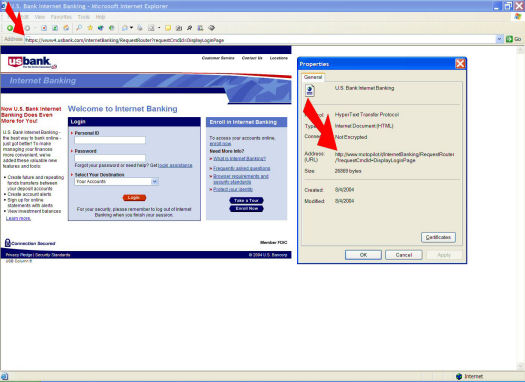
The fake USBank Web site displayed the real site's address for online banking. However, you couldn't highlight or copy the URL as you can for any legitimate Web site. The address wasn't text; it was an image.
On computers with certain display resolutions or browser settings, the image didn't line up, although sometimes it was close. Note the light gray border near the upper left-hand portion of the image in the screen shot. But in browsers where the Web address line takes up part of the allotted space, rather than all of it, the use of the image was obvious. Moreover, if you opted to review the Web page properties (File/Properties), the address retrieved by the browser, and the one displayed in the address line, didn't match.
An Ounce of Prevention
Using these screen shots, or others available at anti-phishing Web sites such as APWG or MillerSmiles, librarians can demonstrate how to detect common tricks and suggest preventive measures. Helpful instruction would not have to be highly technical. It could cover basic safe computing practices, such as the importance of using software firewalls and anti-virus programs. According to a recent survey by the National Cyber Security Alliance, 67 percent of those surveyed did not use up-to-date (within the past week) anti-virus software. The same number did not use any firewall protection.
Basic instruction could also warn consumers not to click links sent by e-mail, especially when they come from an unknown source. It's easy to disguise a target address, and in fact, criminals often use this technique in phishing scams.
Instead, suggest that your patrons get into the habit of copying and pasting the visible Web address into a new browser window. This tactic will also detect a message that consists entirely of an image -- another common phishing technique. Criminals and spam senders often use images instead of HTML to bypass Bayesian filters.
You could also explain the hazards of accepting e-mail in HTML format. In addition to disguising the origin or intent of the information, it facilitates the spread of malware. Many newer e-mail clients give you the option of displaying messages as text. This simple tactic can stop a virus or other malware from activating.
Teaching basic preventive measures as well as the skills necessary to detect common technical tricks could go a long way toward preventing online fraud. It could also improve the evaluative skills needed to identify bad information. Recent surveys and news stories about the victims of online scams indicate that many would benefit from such instruction. In a world where instant gratification is the measure by which many judge the success of their Web searching, these skills could keep them out of trouble -- at least some of the time.